Understanding Cyberthreats: A Comprehensive Guide to Threat Modeling and Proactive Security
In today’s interconnected landscape, cyberthreats loom large and ever-changing. For startups, neglecting digital security is not an option. Delaying action until a security breach occurs can result in significant financial losses and reputational harm.
ExpressVPN recently teamed up with Linking Help, the NGO behind UA.SUPPORT, which offers pro bono legal assistance to Ukrainian refugees, to conduct a threat modeling analysis. The goal was to identify security vulnerabilities and implement effective mitigation strategies. Drawing inspiration from this initiative, we aim to share our methodology with the broader community, empowering startups to bolster their security posture even amidst resource constraints and competing business demands.
Unveiling Vulnerabilities with Threat Modeling
Threat modeling serves as a foundational practice for fortifying digital defenses. Essentially, it entails comprehending and mapping out your organization’s landscape to preemptively thwart potential harm. The objective is to illuminate security gaps and minimize the risk of exploitable vulnerabilities by systematically scrutinizing potential avenues of attack.
While numerous threat modeling standards and frameworks exist, the choice depends on your unique circumstances. Rather than prescribing a specific framework, we’ll delve into the underlying methodology utilized during the threat modeling exercise for UA.SUPPORT, offering pragmatic and efficient security insights.
Actionable Strategies for Startup Resilience
- Understanding Your Adversaries
Identifying potential adversaries and discerning their objectives is paramount for evaluating why and how your startup may become a target. Cybercriminals often set their sights on systems handling credit cards or personally identifiable information (PII), while nation-state actors may seek intelligence for espionage purposes.
For UA.SUPPORT, potential adversaries encompassed:
- Advanced adversaries: Targeting intelligence on Ukrainian individuals, compromising systems for unauthorized access, and disrupting organizational platforms.
- Opportunistic cybercriminals: Exploiting refugee PII for monetary gain, engaging in unauthorized cryptocurrency mining, and utilizing the organization’s infrastructure for malware dissemination.
Once adversaries and their motivations are identified, scrutinizing what they perceive as valuable assets enables the breakdown of potential targeting strategies.
- Know Your Environment
Gaining a comprehensive understanding of your organizational environment is paramount to anticipate how threats may manifest. Engage with internal experts overseeing your systems and processes to glean insights into data flows, system architecture, and operational intricacies. This collaborative effort facilitates the creation of an inventory that encapsulates the complex interplay of business and technological components.
Key areas of examination may include refugee-legal support interactions, information transfer mechanisms, employee access privileges, and system configurations.
- Identifying Weak Points
By formulating hypothesis-driven questions, pinpointing potential weak points susceptible to exploitation becomes feasible. Delve into specific operational domains, such as customer relationship management (CRM) systems and transaction databases, to identify vulnerabilities ripe for exploitation.
For UA.SUPPORT, meticulous analysis of refugee-legal volunteer interactions, including CRM systems and front-facing websites, unveiled critical areas warranting enhanced security measures.
- Putting Yourself in the Adversary’s Shoes
To effectively mitigate vulnerabilities, consider potential pathways adversaries might exploit. Leverage your startup’s intimate knowledge of internal systems to conduct a thorough risk analysis. Employ tools like attack tree diagrams to visualize potential attack scenarios and map out the progression from one compromised point to another.
By asking targeted questions and visualizing attack scenarios, startups can fortify their defenses against evolving cyberthreats, safeguarding critical assets and preserving organizational integrity.
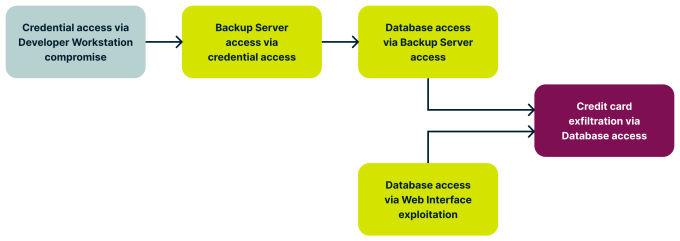
Image Credits: ExpressVPN
Indeed, real-world systems exhibit far greater complexity, often resulting in the creation of attack trees with multiple branches and levels.
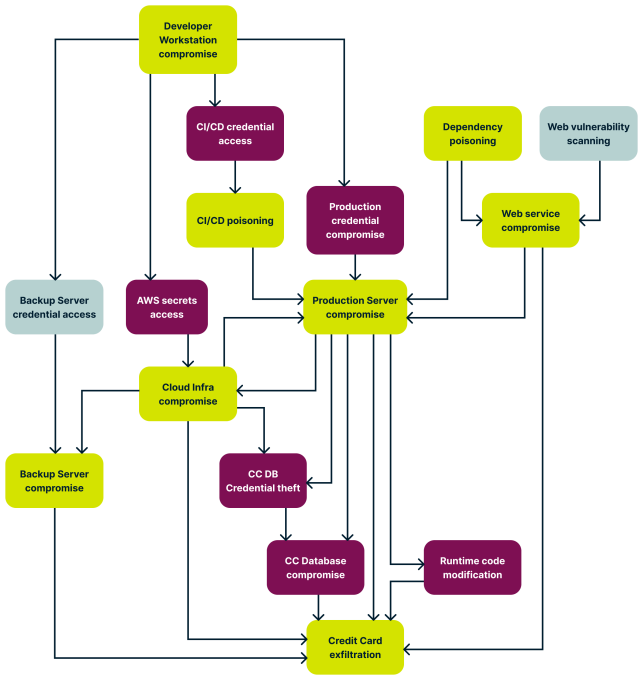
Image Credits: ExpressVPN
By comprehending the system landscape and acquiring responses to these inquiries, you can visualize how attackers might link actions to advance toward their objectives.
- Assign an evilness score To streamline efforts in addressing security risks, implement a scoring mechanism to designate threat levels. This allows for a rapid assessment of the criticality of each step in a potential attack. Several factors can be taken into account when assigning these scores:
Severity: The degree of compromise or harm that an attack could inflict (ranging from 0 [Negligible] to 5 [Highly Severe]). Impact: The consequences of an attack on your daily operations and overall business (ranging from 0 [No Impact] to 5 [High Impact]). Likelihood: The probability of an attack occurring (ranging from 0 [Unlikely] to 5 [Highly Likely]). Capabilities: The expertise and tools required, as well as the level of difficulty an adversary may encounter when attempting to execute the action (ranging from 0 [High Capabilities] to 5 [No Capabilities]). By aggregating the scores for each step, you can gain insight into the potential risks you face and prioritize mitigation efforts based on the most critical threats. This method ensures that resources are directed towards addressing the most pressing areas first.
Once the scores are tallied, you can use this sample scale to assess overall risk:

Image Credits: ExpressVPN
Implementing Proactive Security Measures Once potential vulnerabilities and high-priority threats are identified, it’s essential to take proactive steps to address them. This involves implementing security controls and countermeasures to mitigate the identified risks effectively.
Accept, Mitigate, or Transfer Based on the threat scores, evaluate whether to accept the risks, mitigate them by introducing additional safeguards, or transfer them by leveraging third-party vendors or solutions.
Common proactive security measures include:
Enforcing two-factor authentication for user accounts to prevent unauthorized access. Maintaining software and systems up-to-date to address known vulnerabilities. Providing regular training for employees and volunteers to educate them about security threats and best practices. Implementing secure coding practices to prevent common vulnerabilities like injection attacks and cross-site scripting (XSS). Utilizing encryption to safeguard sensitive data. Deploying intrusion detection and prevention systems (IDPS) to monitor and block malicious activities.
Update Scores As security protections are implemented, it’s crucial to update threat scores accordingly. This ensures a reassessment of the effectiveness of newly implemented security measures by reflecting the likelihood of threats occurring.
Continuously Monitor and Adapt Threat modeling and proactive security measures are ongoing processes. It’s important to regularly review and update threat models as the business and threat landscape evolve. Additionally, fostering a culture of security awareness and accountability throughout the organization encourages employees and volunteers to promptly report any security concerns or incidents.
The Value of Proactive Cybersecurity Strategies Cybersecurity is intricate, and even with thorough threat modeling, there’s always a risk of compromise. However, each proactive step taken to secure systems makes it more challenging for adversaries to compromise them.
The goal isn’t necessarily to be the fastest sprinter but to outrun others being targeted and stay one step ahead. By investing time and effort into proactive cybersecurity strategies, the overall security posture is elevated, increasing the likelihood of staying ahead and effectively protecting digital assets.

