In October (2023), cyber-criminals targeted the British Library, encrypting its data and demanding a ransom. Months later, the library remains offline, underscoring the persistent threat of ransomware attacks. These attacks not only impact businesses but also pose a growing threat to national security, affecting critical infrastructure such as schools, hospitals, and power utilities. Western countries now face a significant risk of a catastrophic ransomware attack, as highlighted by a British parliamentary committee.
While the scale of the problem is challenging to quantify due to underreporting and improved detection, there has been a resurgence in ransomware attacks after a lull in 2022. Officials anticipate 2023 to be a record year for such incidents. The number of victims is on the rise, with leak sites listing the highest-ever recorded victims in the four months leading to October. Individual ransom payments have also increased, averaging over $1.5 million in the first three months of 2023, compared to around $800,000 in 2022. Data indicates a significant financial impact, with estimated ransom payments totaling $449 million between January and June 2023, approaching the 2022 total of $559 million. These figures likely represent only a fraction of the actual problem.
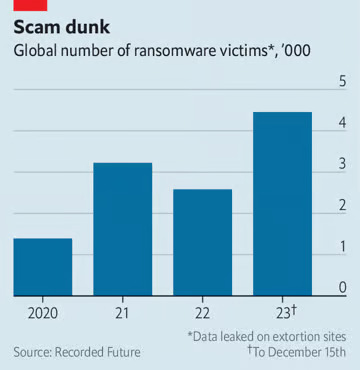
The escalating menace of ransomware is marked by a transformation in its landscape. Once dominated by a few major criminal groups, the scenario is evolving into a mosaic of smaller attackers, many based in Russia or other ex-Soviet states, equipped with readily purchasable hacking tools. Western nations are responding with sanctions and counter-cyber attacks, yet the wave of ransom payments persists, enriching criminal groups and potentially exacerbating the issue for years. While ransomware has primarily been a Western problem, it is spreading globally, affecting countries like America, Australia, Britain, Canada, Germany, Brazil, and India. The targets range from public to private sectors, with recent attacks hitting various entities worldwide, including an Italian cloud-service provider, Germany’s energy agency, and a Chinese bank in New York. This global surge in ransomware poses a significant national-security crisis, with potential to bring a country to a standstill, warns Graeme Biggar, the director of Britain’s National Crime Agency (NCA).
The nature of ransomware has undergone notable changes, driven by factors like the rise of cryptocurrency and the growth of ransomware-as-a-service (RaaS). Cryptocurrency facilitates immediate cashing out for attackers, eliminating the need for complex laundering processes. RaaS allows smaller criminal affiliates to purchase advanced services from specialized providers, leading to a proliferation of smaller groups engaging in ransomware attacks. Online marketplaces like Genesis Market further streamline the trade, offering stolen credentials at low prices, making it easier and cheaper to execute ransomware attacks. This division of labor has resulted in a shift towards smaller groups, with many consisting of just a few individuals. Additionally, the threat landscape is constantly evolving, with an increasing number of ransomware variants and a decreasing dwell time between network intrusion and ransomware execution.
The business model of ransomware has also undergone a transformation. While traditional attacks involved demanding a ransom for decrypting victim data, contemporary attackers often exfiltrate data and threaten to publish it online. In some cases, attackers do not encrypt the data at all. This shift to double or triple extortion, including threats to expose sensitive information, adds complexity to the response landscape. The median dwell time has decreased over the years, giving defenders less time to detect and respond to attacks. Overall, the multifaceted evolution of ransomware poses a formidable challenge to cybersecurity and national security.
Search for vulnerabilities
Halting this phenomenon is exceptionally challenging. The majority of attacks are not directed at a specific business; rather, attackers, much like car thieves checking for unlocked doors, typically send phishing emails widely across a particular sector or exploit cyber vulnerabilities in enterprise products, such as VPN networks. Implementing basic cyber-hygiene practices like data backups, password changes, and software patching could address a significant portion of the problem. However, given human nature, defenses will inevitably have gaps.
The conventional law enforcement response of investigating, arresting, and prosecuting often proves ineffective. While some attackers operate from jurisdictions where cooperation or extradition is viable, many are located in countries like China, Iran, North Korea, and Russia, beyond the reach of Western courts. There exists a spectrum of state complicity, with some Russia-based groups closely tied to the country’s intelligence services, while others are merely tolerated.
This symbiotic relationship likely involves Russian state hackers using ransomware tactics to camouflage their espionage activities, leveraging the talent pool within ransomware groups. The connection extends to foreign-policy goals, with Russia-based groups intensifying attacks before major democratic elections and targeting companies that withdrew from Russia following its invasion of Ukraine.
Despite these challenges, the murky connections between the Russian state and cyber-criminals offer a diplomatic opening. Western governments are increasingly resorting to direct attacks on hackers. Covert activities aim to sow distrust among ransomware group members, disrupting their operations. While such measures have had some success, they are not a panacea. Notable takedowns like those against Hive and Qakbot are rare and resource-intensive.
Another prong of the counteroffensive involves legal measures, with the imposition of sanctions on cyber-criminals by the US and UK. Sanctions target ransomware bigwigs, limiting their ability to travel or spend money abroad. This approach exploits the unique aspect of the criminals’ business model, where trust between attackers and victims is crucial. Sanctions disrupt this trust, potentially forcing groups to abandon established brands.
While some advocate for a complete ban on ransom payments, governments have been reluctant due to concerns that firms might cease reporting attacks and resort to secret payments. Ransom payments often serve as a last resort to keep a business or vital service operational. Instead, the focus is on breaking the narrative that paying a ransom is the only solution. Decrypting data may not always work perfectly, and research shows that paying up does not guarantee immunity from future attacks.
Data leaks, while a concern, can be managed effectively. Australia’s Medibank health insurer, for instance, refused to pay a $10 million ransom and collaborated with intelligence agencies to remove leaked data from the dark web, limiting the impact of the attack. Cyber-insurance is also playing a role, incentivizing policyholders to enhance cybersecurity standards and covering alternatives to ransom payment, such as data recovery.
The fight against ransomware is hindered by a lack of comprehensive data on the threat’s true extent. Better reporting practices, improved cybersecurity standards, and enhanced data on cyber incidents are priorities. Efforts involving sanctions, take-downs, and legal measures have had limited impact so far. Additionally, technological advancements, such as generative AI tools, are empowering attackers, making ransomware syndicates well-resourced, adaptable, and increasingly audacious. The fight against ransomware remains a formidable challenge to national security.

